I have the privilege of being able to work directly with Mux customers on a day to day basis, and I get to experience first hand the amazing applications that they’re building on top of our platform. One of Mux’s features that comes up most often is our webhook infrastructure. These webhook notifications proactively (and asynchronously) notify you of changes within assets and live streams, including granular state changes, such as when a live stream connects, starts recording, and as soon as it’s ready to play. From simply keeping your CMS or DAM up to date with the latest information to passing this info down to your end users, webhooks provide valuable information that you can use to customize and control your application’s user experience without the need to poll an API.
However, at least once a week, I receive a question about validating that these webhook notifications are, in fact, coming from Mux. In today’s world, security on the internet is of the utmost importance, and rightly so; from individual developers to large companies, most of our customers have stringent security requirements and firewalls, limiting their exposure to various attack vectors. With webhooks, there needs to be trust between a company and Mux, and one of the worst things we could do would be to betray that trust. We’d feel as terrible as Alfred, here, were we to not live up to our end of this agreement.
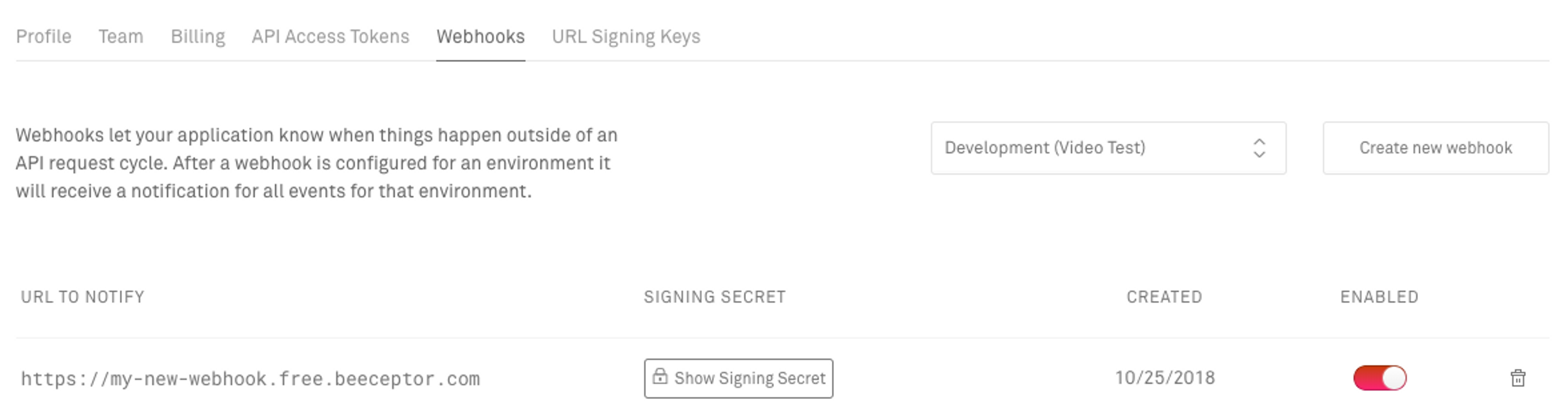
To help ensure that we maintain our side of the bargain, we added an additional security feature for all of our webhooks. Each webhook that you create now comes with a unique signing secret, exposed when you configure the webhook. Don’t worry, existing webhooks have had signing secrets added as well.
Each POST request we make to the configured endpoint now contains a request header, named Mux-Signature, that includes a signature computed with this signing secret. I’ll spare you the gory details for this post (these can be found in our docs), but essentially this signature, along with the signing secret for the webhook, can be used to validate that Mux was the origin for each request, and that there was nobody tampering with the message in between your webhook endpoint and Mux. You can validate the signatures manually, but we’ve also added some helper methods to our Elixir and Node SDKs to make this validation easy. If you’re already using webhooks, fear not! Your current integrations will carry on without any action on your part, so feel free to start validating these signatures once you’re ready.
At Mux, we’re building the tools to help developers build beautiful video applications, and part of this is building secure tools. We will continue to add more features like this to our platform, and we’d love to hear your feedback if you have other suggestions! If you’re new to Mux, sign up here and give it a whirl. We give everyone $20 of free credit to try out Mux Video when you sign up, so try it out!